Santa Cruz CryptoParty
3/25/17
- Why Cryptography Matters - Bennett Roesch
- Basics of Cryptography - Peter Czupil
- Signal - Raymond Colebaugh
- Bitcoin & Blockchains - Sean Gilligan
- Tor & I2P - Raymond Colebaugh
- PGP (Pretty Good Privacy) - Bennett Roesch
- HTTPS Everywhere, TLS, & Let's Encrypt - Peter Czupil
- KeePassX, LastPass, and YubiKey - Bennett Roesch
- OTR & OMEMO - Raymond Colebaugh
- Quantum Cryptography - Ian Gudger
Why Cryptography Matters
Privacy
Security
Identity
"If you have nothing to hide, why be afraid?"
Literally invented by nazis
Crypto is everywhere
- Banking
- Secure browsing
- The credit card chip
- Cell phone transmissions
- Password protected wifi
Basics of Cryptography
Throughout history, these two things have been needed by humans:
- The need to share information
- The need to protect the information they are sharing
- Comes from the combination of (Greek) words Krypto (hidden) and graphene (writing)
 The Spartans wrote on a narrow strip of parchment wrapped around a cylindrical log (called a Scytale) to encrypt messages
The Spartans wrote on a narrow strip of parchment wrapped around a cylindrical log (called a Scytale) to encrypt messages
- Can be defined as: The art and science of concealing messages to introduce secrecy in information security
- From the Oxford dictionary: The art of writing or solving codes
Caesar's Cipher
- Used by the ancient Romans
- To encode "shift" forward the alphabet by a constant offset
- To decode "shift" back

Modern Cryptography
Two types:-
Classic
- Manipulates letters and digits directly
- Based on 'Security through obscurity'
-
Modern
- Operates on binary seqences
- Relies on publicly known mathematical algorithms and computational difficulty
Security of Cryptography
Cryptography provides four services:
- Confidentiality - protects your information from an unauthorized person
- Data Integrity - determines if your message/communication has been tampered with
- Authentication - confirms that a message was sent by a known and verified sender
- Non-repudiation - ensures an entity cannot refuse ownership of a previous action
Secure Mobile Messaging with Signal
What is Signal?

- Signal is a secure communication platform from Open Whisper Systems
- Provides a secure, easy to use alternative to calling, texting, and video chat
- Successor to RedPhone and TextSecure
- Uses data connection instead of phone network
- Signal seamlessly integrates with phone/SMS for the rest of your contacts
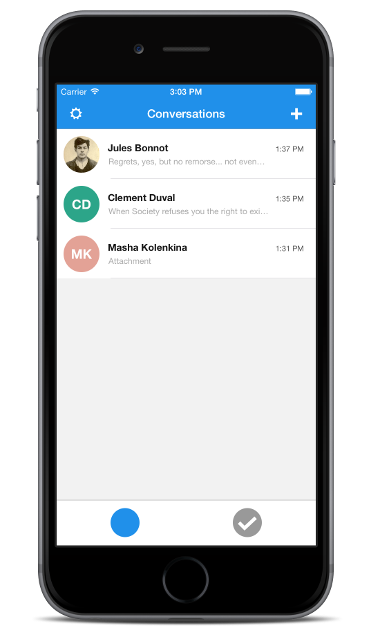
How do I use Signal to communicate?
- Instead of calling your contact, try a Signal voice call
- Instead of sending a text message, send it with Signal. Group chat is supported as well
- You can also video chat (no FaceTime, Allo)
- You can still share pictures and other media
- For contacts without Signal, fallback to the phone network
- Invite your friends to use Signal too!
How does Signal protect my communications?
- Provides end-to-end encryption and authentication for text, audio, and video chat
- Uses the Double Ratchet algorithm, developed by Trevor Perrin and Moxie Marlinspike based on trusted crypto primitives like Curve25519, AES-256, and HMAC-SHA256
- Bunch of other cool privacy features like disappearing messages, key change alerts and verification, and local message db encryption
- Leaves less metadata than using the phone network or other communication apps
Where can I get Signal?
- Signal is available for mobile in the Google Play store and the Apple App Store
- After installing, set Signal as your default SMS application for ease of use
- Signal is also available for desktop as a Chrome app
Bitcoin & Blockchains
Internet Anonymity with Tor and i2p
What are Tor and i2p?


What are Tor and i2p?
- Tor is an anonymous internet proxy that allows users to use the Internet
- Invented at the Naval Research Lab, used by technologists, law enforcement, intelligence services, political activists, and more
- Tor also allows access to onion services, accessible only over Tor
- i2p, the Invisible Internet Project allows access to an alternative anonymous "Internet"
- Initially released in 2003, maintained mostly by pseudonymous developers
How do Tor and i2p help?
- Prevents a website or server from knowing your real IP address
- Prevents your ISP from watching what you do online
- But they do know that you're using Tor (without the use of bridges and the obfuscated pluggable transports) or i2p
- Internet anonymity promotes democracy, free speech and free thought by allowing users to research and express themselves without fear
How do Tor and i2p work?
- Tor uses "onion routing," multiple layers of encryption in a series of relays through a mix network
- By default, a client tunnels through 3 encrypted hops. Each node only knows the next and previous address
- A Tor node can be a middle relay, exit node, or onion service
- i2p uses "Garlic routing," as multiple packets can be encapsulated into a single i2p packet
Differences between Tor and i2p
| Tor | i2p |
|---|---|
| Onion routing | garlic routing |
| Proxy service | private Internet |
| Circuit switched | packet switched |
| TCP only | supports UDP |
| Centralized services | fully decentralized |
| USG funding | anonymous volunteer developers |
Using Tor and i2p as a client
- Tor Browser Bundle
- Avoid fingerprinting by blending in to the crowd
- Tor daemon and proxy configuration
- Useful for CLI tools and other software. See: torsocks(1), proxychains(1)
- Tails Live CD or USB that includes Tor and i2p (for now, v2.11)
- In-memory operating system, wiped on shutdown
Running an Onion Service
- An onion service allows a server to be accessible over a special .onion address
- Configure the HiddenServiceDir and HiddenServicePort directives in the torrc
- Security considerations
- Misconfigurations: disable server-status page
- Vulnerabilities: command injection, server exploits
- Timing attacks: don't run another service, don't run a relay
Running a relay, exit node / router
- If you'd like to support the Tor network, you can run a relay or exit node
-
To run a Tor relay, configure your ORPort and ExitPolicy. For middle relay only,
reject *:* - If you run an exit node, you may get some strange traffic originating from your address
- You can filter most traffic that would attract attention by allowing only HTTPS (443)
- Alternatively, be prepared to explain what Tor is, or have a lawyer to do so
- Note: with i2p, you're a relay by default
Where to get Tor
- Tor is available at https://www.torproject.org/
-
Tor Browser Bundle signing key:
EF6E 286D DA85 EA2A 4BA7 DE68 4E2C 6E87 9329 8290 - Tails is available at https://tails.boum.org/
-
Tails developers signing key:
A490 D0F4 D311 A415 3E2B B7CA DBB8 02B2 58AC D84F - The Orbot Android app is available in the Google Play store
-
Install on Debian and Ubuntu Linux with
sudo apt-get install tor
Where to get i2p
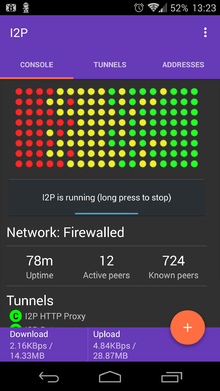
Where to get i2p
- i2p is written in Java (cross-platform)
- i2p is available at https://geti2p.net/
- i2p developers signing key: 2D3D 2D03 910C 6504 C121 0C65 EE60 C0C8 EE72 56A8
- The i2p Android app is available in the Google Play store
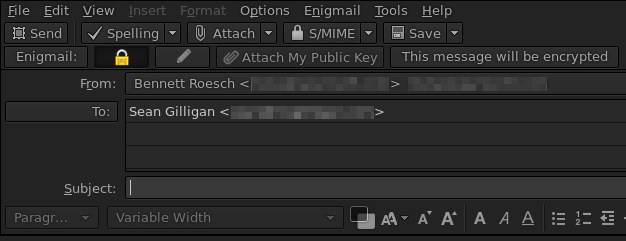
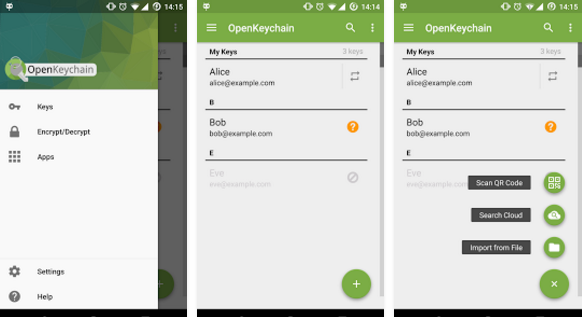
PGP
(Pretty Good Privacy)
Text messages
Emails
Files
Enigmail
Android OpenKeychain
Web of Trust
TLS
HTTPS Everywhere
- Plugin for web browsers
- Tries to force your browser to request web resources over HTTPS
- Available for Chrome, Firefox and Opera
Let's Encrypt
- Project to grant free Domain Verified (DV) SSL certificates
- Free, automated and open source Certificate Authority (CA)
- Operated by the non-profit Internet Security Research Group (ISRG)
Let's Encrypt Cont.
- Free: Anyone who owns a domain name can use Let’s Encrypt to obtain a trusted certificate at no cost
- Automatic: Certbot handles creating, installing and renewing the certificate
- Transparent: All certificates issued or revoked are available to the public
- Secure: Promotes TLS security best practices
- https://letsencrypt.org/
Transport Layer Security
(AKA Secure Sockets Layer)
What is it?
- Protocol used for secure electronic communications
- Designed to prevent eavesdropping and tampering
- Used in many applications such as web browsing, email and text-messaging
- Practical form of public key cryptography
- Also referred to as "Secure Sockets Layer" or "SSL"
How Does it Work?
- The communication between two devices is encrypted using a shared secret
- The shared secret is only known to the devices communicating
- Each message received is decrypted using a code known only to the receiver
Best Practices
- Do not browse websites which don't have valid SSL certificates
- Use more technology which was developed with security in mind
- Do not use any versions of the SSL protocol, use TLS instead (preferably TLSv1.2)
Useful Technologies
- Let's Encrypt/Certbot
- HTTPS Everywhere
- https://badssl.com/
KeePassX, LastPass, and YubiKey
Password Managers
- Long Random Passwords
- Password Diversity
- Fights Key Loggers
- How Passwords Are Compromised
- Sending Passwords Via Email
- Good Keychain Password = Passphrase
YubiKey

- Onetime Passwords
- Public Key Encryption
Secure Instant Messaging with OTR and OMEMO
What is OTR?
- "Off The Record" messaging over instant messaging protocols like XMPP and AIM
- Extends IM with encryption, authentication, forward secrecy, and deniable authentication
- OTR supports file transfers (since version 3)
How do I use OTR?
- OTR can be installed as an extension to many popular instant messaging clients, such as Pidgin
- The Android app Xabber also supports OTR for secure instant messaging on the go
- Many clients can be configured to automatically initiate an OTR session
How does OTR protect my communications?
- Encrypts your communication from prying eyes
- Based on AES-128, Diffie-Hellman, and SHA-1
- Authenticates your communicating party
- Provides deniable encryption
Where do I get OTR?
- Available as a plugin for Pidgin (cross platform)
- Natively supported by
- Adium on OS X
- Kopete on UNIX-like systems
- Xabber and Conversations for Android
- ChatSecure for iOS
What is OMEMO?
- Next generation OTR with encrypted group chat support
- Introduced in Google Summer of Code 2015 to Conversations for Android
- Also offers forward secrecy and deniable encryption
How is OMEMO different than OTR?
- Supports group chat (multi-client end-to-end encryption)
- OMEMO uses the Double Ratchet algorithm (Signal)
Where can I get OMEMO?
- Originally written for Conversations for Android
- ChatSecure for iOS supports OMEMO
- Cross-platform client Gajim supports OMEMO through a plugin
Bonus: Anonymous, encrypted messaging with Ricochet
- Dedicated, Tor-based instant messenger
- Use Tor onion addresses instead of usernames or nick names
- End-to-end message encryption
- No central servers or middle man
- Eliminates conversation metadata
- Soon to support file transfers (or use OnionShare)
Quantum Cryptography
Quantum changes everything
- Quantum breaks common cryptography
- Quantum enables new better cryptography
There are two types of traditional cryptography
- Symmetric
- Asymmetric
Symmetric
- Encrypt and decrypt keys are the same
- Key exchange is hard
- Typically very fast
- Used for encrypting data
Asymmetric
- Encrypt and decrypt keys are different
- Typically very slow
- Mostly used for encrypting symmetric encryption keys
Common Asymmetric Encryption
- RSA
- Depends on the assumption that factoring a product of two very large prime numbers is hard
- Diffie–Hellman/ElGamal
- Depends on the assumption that the discrete log problem is hard
Quantum computing breaks common cryptography
- Shor's algorithm
- Uses a quantum computer to efficiently factor very large numbers
- Also works for discrete logs
- Symmetric is thought to be mostly safe
Quantum enables new better cryptography
- Quantum mechanics provide useful guarantees
- It is impossible to copy data encoded in a quantum state
- The very act of reading data encoded in a quantum state changes the state